Sitemap
A list of all the posts and pages found on the site. For you robots out there is an XML version available for digesting as well.
Pages
Posts
Future Blog Post
Published:
This post will show up by default. To disable scheduling of future posts, edit config.yml and set future: false.
Blog Post number 4
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Blog Post number 3
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Blog Post number 2
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Blog Post number 1
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
portfolio
Intrusion Detection Systems (IDS) for Controller Area Networks (CAN) Bus
Our research focuses on improving the security of Controller Area Networks (CAN) in modern vehicles, which are increasingly dependent on interconnected electronic control units (ECUs) for critical functions. The CAN protocol, designed for reliability and efficiency, lacks built-in security measures, making it vulnerable to sophisticated cyberattacks that exploit these gaps. Traditional IDS methods, which monitor timing and message sequences, are inadequate against advanced attacks that manipulate signal semantics. Our work addresses these challenges by developing detection systems that can identify such subtle intrusions, enhancing the overall security of vehicular networks. 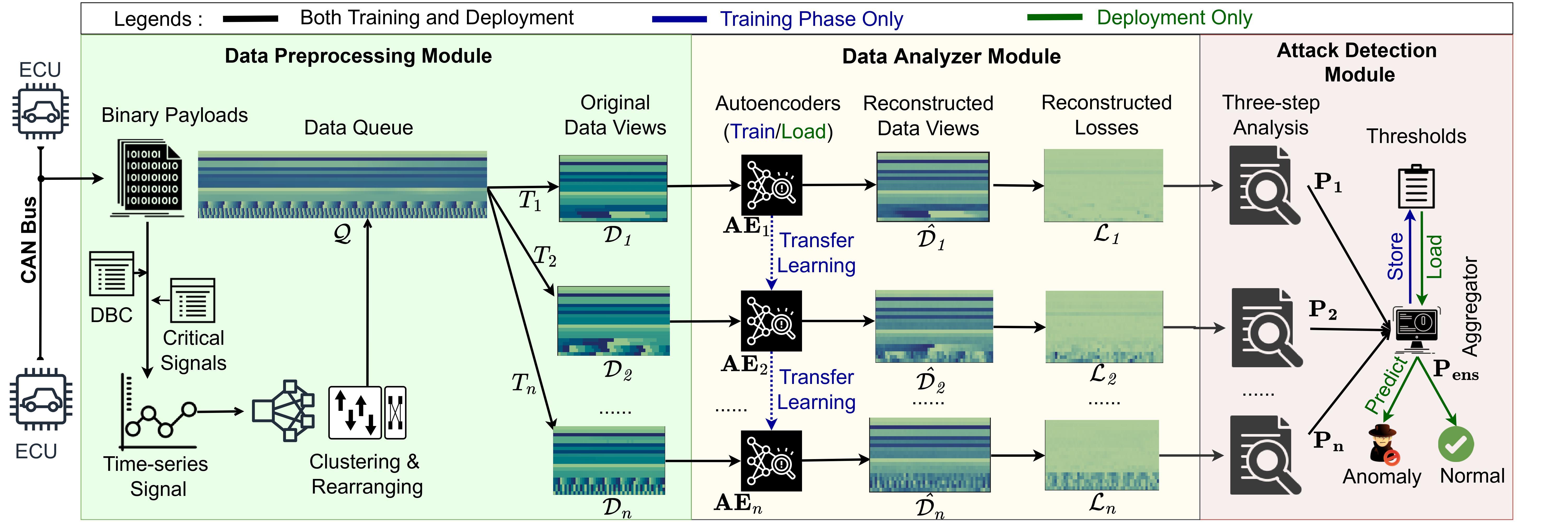
Robust Misbehavior Detection System (MBDS) For Vehicle-to-Everything (V2X) Communication
Our research addresses the pressing need for robust misbehavior detection systems (MBDS) in Vehicle-to-Everything (V2X) communication networks, which are essential for modern intelligent transportation systems. V2X networks face significant security challenges due to their open, decentralized nature, which exposes them to advanced adversarial attacks that can evade traditional machine learning-based detection systems. To overcome these issues, we develop Vehicular GAN (VehiGAN), an advanced MBDS leveraging Generative Adversarial Networks (GANs). VehiGAN enhances anomaly detection and offers strong resilience against adversarial manipulations, improving the security and reliability of V2X communications.. 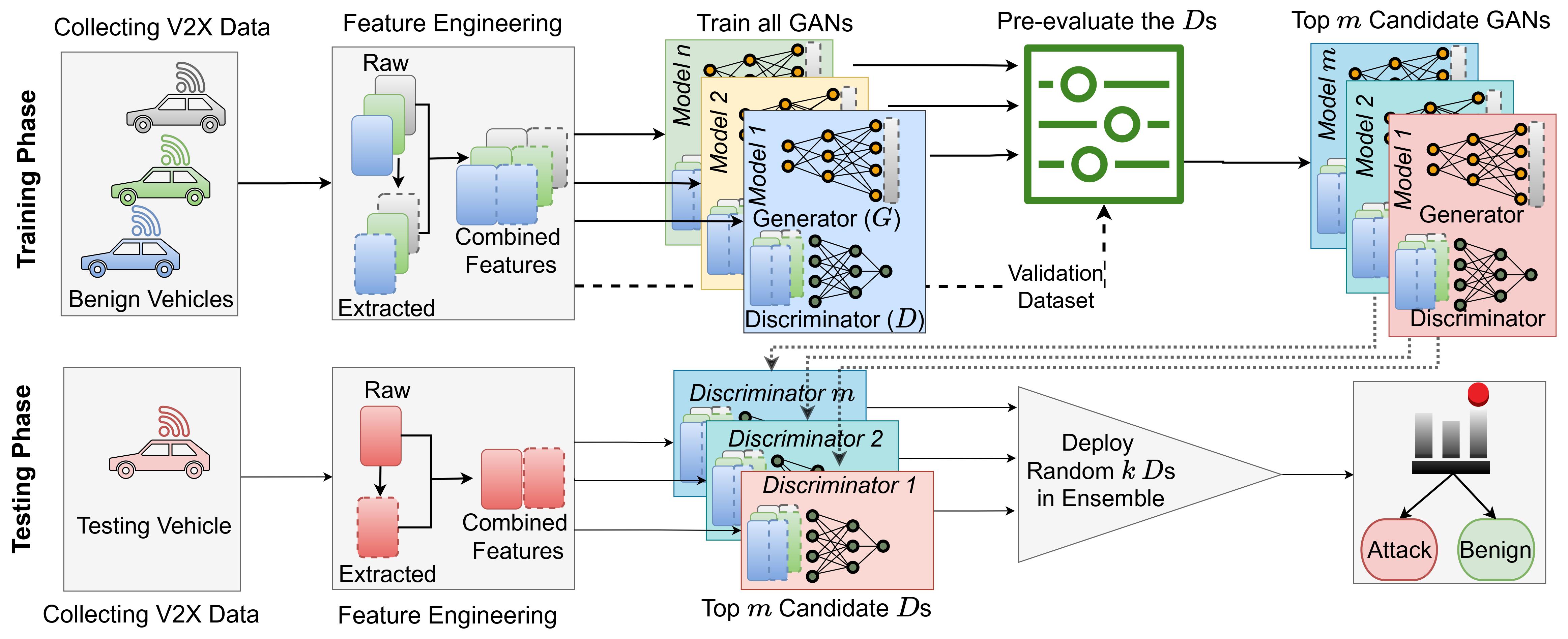
publications
G-IDS: Generative Adversarial Networks Assisted Intrusion Detection System
Published in IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC), 2020
This paper proposes a generative adversarial network (GAN)-based intrusion detection system (G-IDS).
Recommended citation: Shahriar, M. H., Haque, N. I., Rahman, M. A., & Alonso, M. (2020, July). G-ids: Generative adversarial networks assisted intrusion detection system. In 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC) (pp. 376-385). IEEE.
Download Paper
MS Thesis: Defense by Deception against Stealthy Attacks in Power Grids
Published in Florida International University, 2020
This thesis proposed DDAF, a deceptive data acquisition framework for CPS hierarchical communication network.
Recommended citation: Shahriar, Md Hasan. "Defense by Deception against Stealthy Attacks in Power Grids." (2020).
Download Paper
DDAF: Deceptive Data Acquisition Framework against Stealthy Attacks in Cyber-Physical Systems
Published in EEE 45th Annual Computers, Software, and Applications Conference (COMPSAC), 2021
This paper proposed a deception defense-based data acquisition framework for any hierarchical CPSs network.
Recommended citation: Shahriar, M. H., Rahman, M. A., Haque, N. I., & Chowdhury, B. (2021, July). DDAF: Deceptive Data Acquisition Framework against Stealthy Attacks in Cyber-Physical Systems. In 2021 IEEE 45th Annual Computers, Software, and Applications Conference (COMPSAC) (pp. 725-734). IEEE.
Download Paper
False Relay Operation Attacks in Power Systems with High Renewables
Published in IEEE Power & Energy Society General Meeting (PESGM), 2021
This paper analyzed the feasibility of launching False Data Injection (FDI) attack in the power systems with high renewables.
Recommended citation: Jafari, M., Shahriar, M. H., Rahman, M. A., & Paudyal, S. (2021, July). False relay operation attacks in power systems with high renewables. In 2021 IEEE Power & Energy Society General Meeting (PESGM) (pp. 01-05). IEEE.
Download Paper
iAttackGen: Generative Synthesis of False Data Injection Attacks in Cyber-physical Systems
Published in The 9th IEEE Conference on Communications and Network Security (CNS), 2021
This paper proposed a generative adversarial networks (GAN)-based threat analysis framework for CPS.
Recommended citation: Shahriar, M. H., Khalil, A. A., Rahman, M. A., Manshaei, M. H., & Chen, D. (2021, October). iattackgen: Generative synthesis of false data injection attacks in cyber-physical systems. In 2021 IEEE Conference on Communications and Network Security (CNS) (pp. 200-208). IEEE.
Download Paper
iDDAF: An Intelligent Deceptive Data Acquisition Framework for Secure Cyber-Physical Systems
Published in 17th EAI International Conference on Security and Privacy in Communication Networks (SecureComm), 2021
This paper proposed an intelligent deception defense-based data acquisition framework for hierarchical CPSs network.
Recommended citation: Shahriar, M. H., Rahman, M. A., Haque, N. I., Chowdhury, B., & Whisenant, S. G. (2021). iDDAF: An Intelligent Deceptive Data Acquisition Framework for Secure Cyber-Physical Systems. In Security and Privacy in Communication Networks: 17th EAI International Conference, SecureComm 2021, Virtual Event, September 6–9, 2021, Proceedings, Part II 17 (pp. 338-359). Springer International Publishing.
Download Paper
CANtropy: Time Series Feature Extraction-Based Intrusion Detection Systems for Controller Area Networks
Published in Symposium on Vehicles Security and Privacy (VehicleSec), 2023
This paper proposed a manual feature engineeringbased lightweight IDS for controller area network (CAN) bus.
Recommended citation: Shahriar, M. H., Lou, W., & Hou, Y. T. (2023). CANtropy: Time series feature extraction-based intrusion detection systems for controller area networks. In Proc. of Symp. on Vehicles Security and Privacy (VehicleSec) (pp. 1-8).
Download Paper
MS-PTP: Protecting Network Timing from Byzantine Attacks
Published in 16th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2023
This paper present the security vulnerabilities of precision time protocol (PTP) and discuss limitations of existing defenses.
Recommended citation: Shi, S., Xiao, Y., Du, C., Shahriar, M. H., Li, A., Zhang, N., Hou, Y, & Lou, W. (2023). Ms-ptp: Protecting network timing from byzantine attacks. In Proceedings of the 16th ACM Conference on Security and Privacy in Wireless and Mobile Networks (pp. 61-71).
Download Paper
CANShield: Deep-Learning-Based Intrusion Detection Framework for Controller Area Networks at the Signal Level
Published in IEEE Internet of Things Journal, 2023
This paper proposed a deep learning-based signal level intrusion detection framework for the controller area network (CAN) bus.
Recommended citation: Shahriar, M. H., Xiao, Y., Moriano, P., Lou, W., & Hou, Y. T. (2023). CANShield: Deep Learning-Based Intrusion Detection Framework for Controller Area Networks at the Signal-Level. IEEE Internet of Things Journal.
Download Paper
Formal Analytics for Stealthy Attacks Against Contingency Analysis in Power Grids
Published in Sustainable Energy, Grids and Networks, 2024
This paper formally model complex attacks on power grid contingency analysis and solve them using Satisfiability Modulo Theories (SMT)
Recommended citation: Shahriar, M. H., Rahman, M. A., Jafari, M., & Paudyal, S. (2024). Formal analytics for stealthy attacks against Contingency Analysis in power grids. Sustainable Energy, Grids and Networks, 38, 101310.
Download Paper
VehiGAN: Generative Adversarial Networks for Adversarially Robust V2X Misbehavior Detection Systems
Published in 44th IEEE International Conference on Distributed Computing Systems (ICDCS), 2024
This paper proposed a generative adversarial networks (GAN)-based efficient and adversarially robust MBDS for V2X.
Recommended citation: Shahriar, M. H., Ansari, M. R., Monteuuis, J.-P., Chen, C., Petit, J., Hou, Y. T., & Lou, W. (2024). VehiGAN: Generative adversarial networks for adversarially robust V2X misbehavior detection systems. In Proceedings of the 44th IEEE International Conference on Distributed Computing Systems (ICDCS).
Download Paper
Let the Noise Speak: Harnessing Noise for a Unified Defense Against Adversarial and Backdoor Attacks
Published in 30th European Symposium on Research in Computer Security (ESORICS), 2025, 2025
This paper proposes NoiSec that disentangles the noise from the test input, extracts the underlying features from the noise, and leverages them to recognize systematic malicious manipulation (adversarial or backdoor)
Recommended citation: Shahriar, M. H., Wang, N., Ramakrishnan, N., Hou, Y. T., & Lou, W. (2024). Let the Noise Speak: Harnessing Noise for a Unified Defense Against Adversarial and Backdoor Attacks. 30th European Symposium on Research in Computer Security (ESORICS), 2025
Download Paper
VehiGAN: Generative Adversarial Networks for Adversarially Robust V2X Misbehavior Detection Systems
Published in ACM Transactions on Cyber-Physical Systems, 2025
This paper is the extension of the ICDCS paper on generative adversarial networks (GAN)-based efficient and adversarially robust MBDS for V2X.
Recommended citation: Shahriar, M. H., Ansari, M. R., Monteuuis, J.-P., Haque, M. S., Chen, C., Petit, J., Hou, Y. T., & Lou, W. (2025). VehiGAN: Generative adversarial networks for adversarially robust V2X misbehavior detection systems. ACM Transactions on Cyber-Physical Systems (ACM TCPS), Just Accepted. https://doi.org/10.1145/3745787
Download Paper
talks
Talk 1 on Relevant Topic in Your Field
Published:
This is a description of your talk, which is a markdown files that can be all markdown-ified like any other post. Yay markdown!
Conference Proceeding talk 3 on Relevant Topic in Your Field
Published:
This is a description of your conference proceedings talk, note the different field in type. You can put anything in this field.
teaching
Teaching experience 1
Undergraduate course, University 1, Department, 2014
This is a description of a teaching experience. You can use markdown like any other post.
Teaching experience 2
Workshop, University 1, Department, 2015
This is a description of a teaching experience. You can use markdown like any other post.
